LAN Scan shows me Sasser Worm at 445 port.
-
Hi People! yesterday i scaned my network for new mobile devices (family came to visit us) .. im always scan using Fing (android app) but i tryed another one, Scanner LAN app... and for my Asus Thinkerboard with Retropie it shows the opened ports, SO... one strange thing came up; the shared port 445 mentions that is a Active Directory, Window's Share, Sasser-worm.
Screen shot:
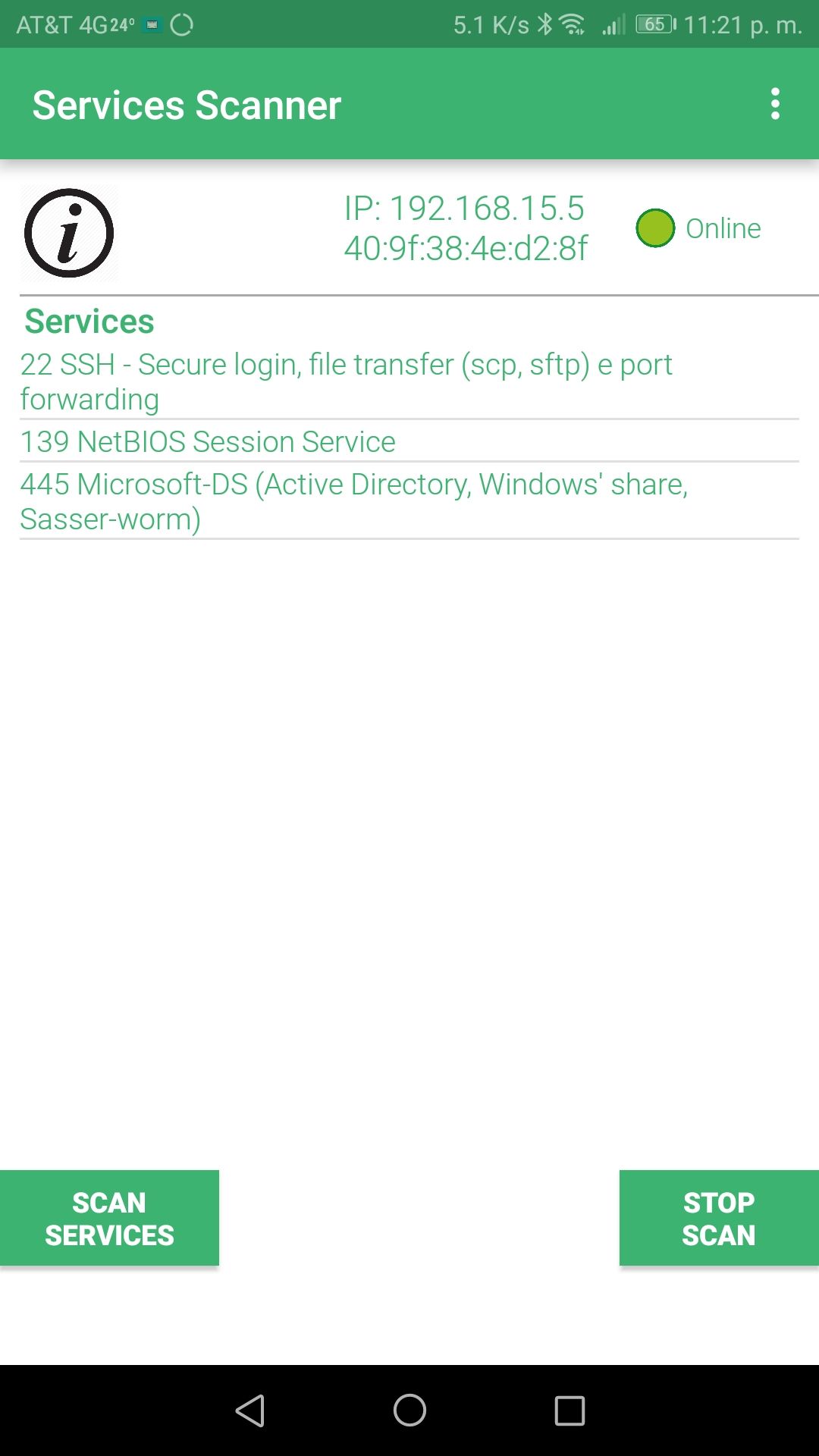
So, there's a worm inside retropie? i checked that Sasser is for older Windows, also i have chequed the RPI using ClamAV and it seems to be clean, searching more deeper, i found that can use another tool, Linux Malware Detect+ClamAV (https://www.tecmint.com/install-linux-malware-detect-lmd-in-rhel-centos-and-fedora/2/) ... its still scanning the full linaroOS.
I should worry about this distro? if some one else can scan your LAN to see if realy says it's infected using the same Scanner LAN app.
-
@thejavi There is no 'Sasser-worm' in RetroPie. The listing next to the 445/TCP port enumerates the possible programs that might be using that port. 445/TCP is the standard port for Windows file sharing service that allows you to copy your ROMs over to RetroPie and it's used by the Samba service.
-
@mitu yep, i know that.. but, my paraonia (after seeing Mr Robot series) was incremented.. xD
this is the result of the LMD:
HOST: tinkerboard
SCAN ID: 190505-1410.8203
STARTED: May 5 2019 14:10:21 -0500
COMPLETED: May 5 2019 16:31:50 -0500
ELAPSED: 8489s [find: 30s]PATH: /
TOTAL FILES: 41178
TOTAL HITS: 12
TOTAL CLEANED: 0WARNING: Automatic quarantine is currently disabled, detected threats are still accessible to users!
To enable, set quarantine_hits=1 and/or to quarantine hits from this scan run:
/usr/local/sbin/maldet -q 190505-1410.8203FILE HIT LIST:
{YARA}r57shell_php_php : /opt/retropie/configs/all/retroarch/shaders/shaders_glsl/crt/crt-royale-pal-r57shell.glslp
{YARA}r57shell_php_php : /opt/retropie/configs/all/retroarch/shaders/shaders_glsl/pal/pal-r57shell.glslp
{YARA}r57shell_php_php : /opt/retropie/configs/all/retroarch/shaders/shaders_glsl/pal/pal-r57shell-moire-only.glslp
{YARA}r57shell_php_php : /opt/retropie/configs/all/retroarch/shaders/shaders_glsl/pal/shaders/pal-r57shell.glsl
{YARA}r57shell_php_php : /opt/retropie/configs/all/retroarch/shaders/shaders_glsl/pal/shaders/pal-r57shell-moire-only.glsl
{YARA}Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php : /home/linaro/Downloads/maldetect-1.6.4/files/sigs/md5.dat
{HEX}php.gzbase64.inject.452 : /home/linaro/Downloads/maldetect-1.6.4/files/sigs/rfxn.yara
{YARA}Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php : /home/linaro/Downloads/maldetect-1.6.4/files/sigs/rfxn.hdb
{YARA}Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php : /home/linaro/Downloads/maldetect-1.6.4/files/sigs/rfxn.ndb
{YARA}Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php : /home/linaro/Downloads/maldetect-1.6.4/files/sigs/md5v2.dat
{YARA}Safe0ver_Shell__Safe_Mod_Bypass_By_Evilc0der_php : /home/linaro/Downloads/maldetect-1.6.4/files/sigs/hex.dat
{HEX}php.gzbase64.inject.452 : /home/linaro/Downloads/maldetect-1.6.4/files/clean/gzbase64.inject.unclassedLinux Malware Detect v1.6.4 < proj@rfxn.com >
-
Well, all this are safe, the log was returned a false positive from that PHP file.
Contributions to the project are always appreciated, so if you would like to support us with a donation you can do so here.
Hosting provided by Mythic-Beasts. See the Hosting Information page for more information.